The developers of the open-source virus scanner ClamAV are presenting three new versions that, among other things, fix two serious security gaps. In addition, the brand new edition 1.3.0 brings support for OneNote files.
Advertisement
Command smuggling via format string
Both LTS versions 1.0.0 to 1.0.4 and ClamAV 1.2.0 and 1.2.1 contained a bug in the processing of the name of a scanned file that has serious consequences. The vulnerability with the CVE ID CVE-2024-20328 can be exploited remotely by an attacker to force a ClamAV server to execute arbitrary commands.
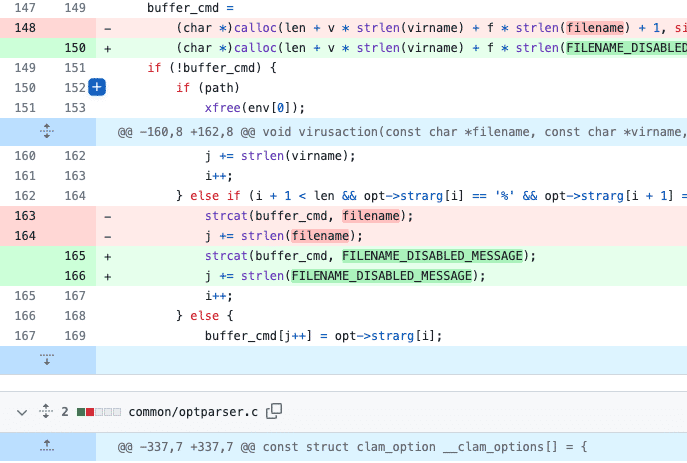
Comparison of ClamAV versions 1.2.1 and 1.2.2. Marked red in line 163: The potentially malicious file name is adopted without being checked.
(Image: heise security / cku)
The error is hidden in the configuration directive VirusEvent, which is actually intended to execute a command when a virus is found. This can be useful to notify the admin or copy the infected file to a special quarantine directory. The directive allows the admin to set the file name using the variable %f into the command – and does not check this variable before passing the command to the operating system.
Since this error can be exploited over the Internet without additional permissions, the CVSS value is likely to be correspondingly high. However, no official assessment of the severity has yet been published – heise security expects the security breach to be… critical is classified, possibly even with the highest possible CVSS value of 10. The explorer Amit Schendel describes his find in a detailed blog article.
In addition to the versions mentioned above, all versions of version 1.1 and versions 0.104 and 0.105 are also affected by the vulnerability.
ClamAV chokes on OLE2
However, a second security problem in the antivirus software “only” causes ClamAV to get out of step and refuse to work. ClamAV 1.0.0 to 1.0.4, 1.2.0 and 1.2.1 as well as all 1.1 versions are also vulnerable.
The cause here is a buffer overflow in the heap when trying to process a file with OLE2 data. Attackers exploiting this vulnerability (CVE-2024-20290, severity “high“, CVSS 7.5/10) can cause the current ClamAV process to crash, but cannot execute your own commands.
ClamAV has released bug-fixed versions with version numbers 1.0.5 and 1.2.2. Admins should patch quickly, but the major Linux distributions have not yet responded. If you’re still using ClamAV 1.1, you should switch to a newer version; you’ll lose out on bug fixes in the 0.x versions Blog article about the update but not a word.
It is also unclear whether the brand new version 1.3.0 fixes the security problems – but the assumption is reasonable. ClamAV 1.3.0 also brings support for OneNote attachments, which can be turned on or off via a configuration directive or via the command line. ClamAV can now also check compiled Python files with the usual .pyc extension for malware. This is a welcome addition, as there is always malware in repositories like PyPi.
Cisco products are also affected
ClamAV, which celebrated its 20th anniversary last year, is being further developed under the leadership of Cisco. For its part, the network supplier warns in one separate safety notice from the impact of the denial of service bug on its own products. The Secure Endpoint Connector for Windows and the Secure Endpoint Private Clouds product contain the malicious code and have been repaired from versions 7.5.17 and 8.2.1 (Endpoint Connector for Windows) and 3.8.0 (Secure Endpoint Private Cloud).
(cku)

