IT security researchers have found that Apple’s Safari web browser does not adequately protect against side channel attacks on processors. Attackers can therefore steal sensitive data using manipulated websites. There are initial protective measures.
Advertisement
The IT researchers come from the Ruhr University Bochum, Georgia Tech and the University of Michigan. With the vulnerability called iLeakage, they now show that Apple’s countermeasures in macOS and iOS do not adequately protect against the misuse of the “Spectre” processor hardware vulnerability. These enable side channel attacks to gain access to actually protected data from other processes. An analysis by c’t editor Andreas Stiller clearly explains the basic problem of Specter and the similar Meltdown.
Apple vulnerability “iLeakage” with its own website
The researchers have set up their own website about the security gap, ileakage.com. There are, among other things, videos available that demonstrate the misuse of the vulnerability: Manipulated websites can therefore spy on access data and website content. The concrete examples show how the prepared website runs in the same process as the attacked site. This shouldn’t normally happen because each website runs in its own process and process isolation isolates the respective RAM. However, the IT researchers were able to use the Javascript function in Safari window.open() to open the website to be attacked, causing the browser to use the same rendering process.
The malicious site then reads log-in data for Instagram from the log-in window in the background by exploiting the CPU side channel, which was automatically entered by a password manager. Another clip shows her grabbing subject lines from Gmail. Or she can access YouTube video history on iOS using the Chrome web browser, since Chrome in the mobile operating system is just an add-on to Safari’s browser engine.
More generally, malicious websites can read content from websites using Javascript and web assembly on macOS, iOS and iPadOS from Safari and web browsers based on it – such as passwords, personal information or even credit card information. The IT researchers at the Ruhr University Bochum explain “Apple is now offering the first software updates for Safari that aim to fix the vulnerability. Further updates are in the works.”
On the iLeakage page, the IT researchers explain how Apple users can protect themselves – thanks to Safari 17.1, which was released on Tuesday for macOS 12 (Big Sur) and macOS 13 (Ventura), this is even easier than it was there explained first. Under macOS 14(.1) (Sonoma) as well as 12 and 13 with Safari 17.1, you first activate the command in the terminal defaults write com.apple.Safari IncludeInternalDebugMenu 1 the browser’s debug menu. The resulting debug menu then provides information below WebKit Internal Features the point Swap Processes on Cross-Site Window Open, which those affected must tick. This activates the protection mechanism against the attack shown.
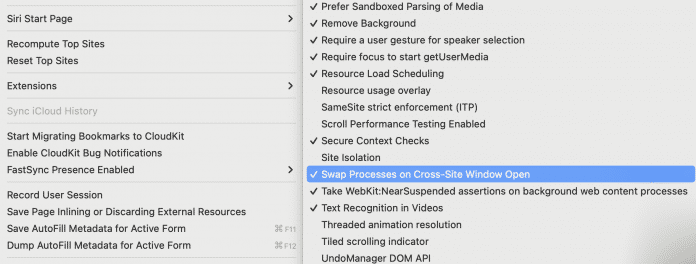
An option hidden in the Safari web browser’s debug menu enables iLeakage protection.
(Image: Screenshot Mac and I, Ben Schwan)
The attack exploits inadequacies in Safari’s Javascript engine. Therefore, other web browsers on macOS are not vulnerable to iLeakage. On iOS and iPadOS, web browsers still cannot have their own engines, but have to be based on Safari. Therefore, these browsers are also vulnerable on Apple mobile operating systems.
The provides more detailed insights Research paper “iLeakage: Browser-based Timerless Specualtive Execution Attacks on Apple Devices”which the IT researchers want to present at the Conference on Computer and Communications Security (CCS) 2023 in Copenhagen at the end of November.
(dmk)

