Malwarebytes virus analysts have discovered a malvertising campaign on Google whose masterminds appear to be targeting system administrators. The advertising lures potential victims to fake websites that plant malware instead of the software they are looking for.
Advertisement

The fake sites appear convincing at first glance and are intended to offer potential victims installers loaded with malware.
(Image: Malwarebytes)
In one Write a blog post by Malwarebytes IT researchersthat when you search on Google for popular system tools such as the terminal emulator with extensive protocol support PuTTY or the FTP program Filezilla, malicious advertising is displayed, especially in North America. The attackers want to trick victims into downloading and running the Nitrogen malware, which is disguised as the software they are looking for.
Google is watching the action so far
The Nitrogen malware bundled in installer packages is used by attackers to gain initial access to private networks. This was followed by data theft and the distribution of ransomware like that from BlackCat/AlphV. The virus analysts have reported the malicious advertisements to Google, but so far nothing has been done about it, they state in their article.
When you search, advertisements appear above the search results. The text describes, for example, that it goes to “PuTTY | Offical Website”, i.e. the official website. However, the link above points to a domain that does not match.
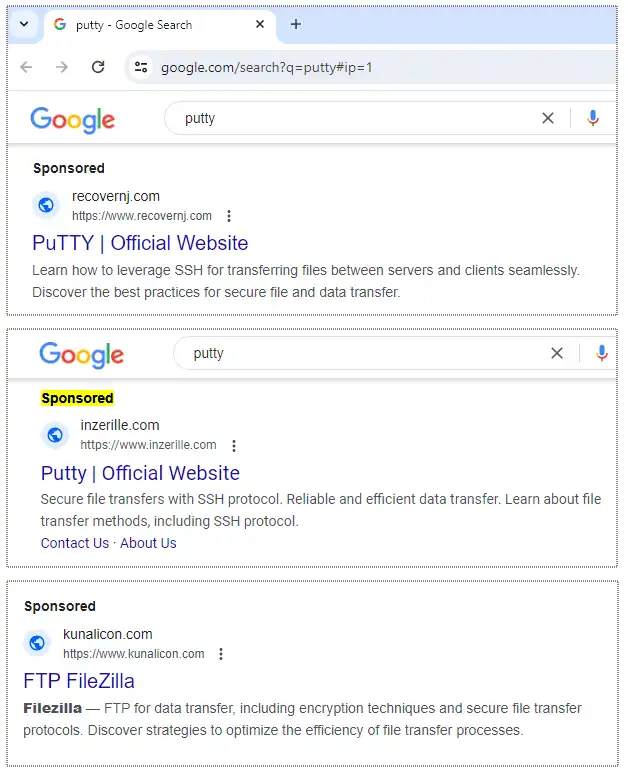
Advertisements on Google claim to link to official sites but redirect to malware sites.
(Image: Malwarebytes)
If victims click on it, they are redirected to websites that look similar to the original. If the specific malware campaign has not yet been fully developed or the malicious server detects unwanted traffic from bots, crawlers or known IP addresses that supposedly belong to virus laboratories, it redirects to a well-known Rick Astley video – a classic one Rickroll (the unexpected playing of the song “Never gonna give you up”).
After downloading the offered file, an installer package will be found on the drive that contains a legitimate and signed executable file that executes a DLL containing the Nitrogen malware via so-called “DLL sideloading”. Specifically, the virus researchers have a Pythonsetup.exe found the malware from the file python311.dll has reloaded. The analysis also contains a few Indicators of Compromise (IOCs), i.e. indications of an infestation that those interested can look for.
Google’s AI search “Search Generative Experience” (SGE) is not immune to malicious advertising. Since the search results there are embedded in explanatory texts instead of just appearing as a more or less “naked collection of links”, they are even more likely to tempt potential victims to visit the malware offerings.
(dmk)

