In a research paper, IT security researchers Yu Chen from Tencent and Yiling He from Zhejiang University have presented an attack on access protection using fingerprint sensors in standard smartphones. The BrutePrint attack enables a brute force attack on many devices. Law enforcement agencies in particular may be interested.
The requirements for BrutePrint limit the possibilities somewhat – it is not possible to simply crack a smartphone at the next table. Attackers need physical access to the cell phone for several hours. You must at least remove the back cover and attach your own hardware to the biometric sensor’s SPI bus. The mobile phone must not restart under any circumstances, since an unlock pattern or a PIN is usually required for access when restarting.
BrutePrint: Many devices affected
As Chen and He explain, they have identified several vulnerabilities, although not every smartphone examined is affected by each. iOS devices did the best. No brute force attack could be carried out on them.
When attempting authentication via fingerprint, the check runs in a loop and usually examines several, but a limited number of fingerprint images. This serves to compensate for technical shortcomings. In addition, a 100% hit does not have to be achieved, but a substantial match is already sufficient for a positive test result.
Any number of attempts
Error, Success, Non-live, or reaching the maximum number of scanned fingerprint images will break the loop. Also, the other possible result, Failed, increases the authentication attempt count; this includes crossing too many non-positive fingerprint images in the loop.
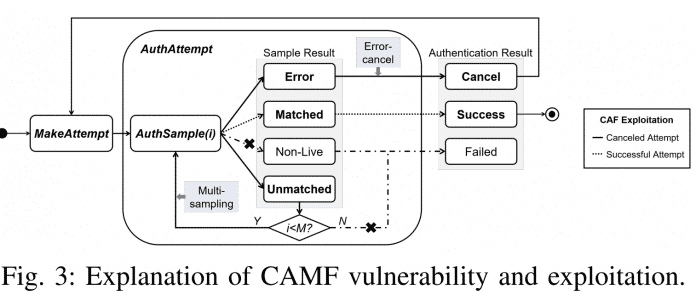
Fingerprint authentication flowchart: By canceling early, Chen and He gain infinite login attempts.
(Picture: Research paper on BrutePrint by Chen (Tencant) and He (Uni Zhejiang))
The IT researchers call one of the security gaps Cancel-After-Match-Fail (CAMF). CAMF allows attackers to trigger an “Error-Cancel” path before reaching the maximum number of fingerprint images examined in the loop, which aborts the attempt. This resets the counter and allows further fingerprint images to be checked. This bypasses the “Failed” result, does not increase the authentication attempt count, and lets attackers try as many fingerprints as they like.
The vulnerability called Match-After-Lock (MAL), on the other hand, concerns the blocking of further authentication attempts for a certain period of time after too many failed attempts. However, some smartphones use a pseudo lockout function. It also prevents login with fingerprints, but fingerprint verification continues in the background in the Trusted Execution Environment (TEE) of the device processor. The result of the check can be derived via a side channel, for example by means of differences in response times and the number of transmitted images. MAL thus also enables a brute force attack with an unlimited number of attempts.
Man-in-the-Middle: Attack on the SPI bus
The biometric fingerprint sensor is connected to the processor via an SPI bus. SPI offers very simple data transfer and is widely used in audio, microprocessor and sensor areas. According to the researchers, apart from Apple’s TouchID, no sensor has yet used encryption or authentication on the SPI bus. This allows the communication on the SPI bus to be manipulated.
The inexpensive, home-made hardware latches into the data lines and can listen there, but also intersperse its own signals (glitching). Ultimately, a fingerprint image can be read out or replaced. Each smartphone or sensor uses a different format, which the attackers have to adapt their smuggled images to. Open-source databases with numerous fingerprints serve as the basis. They adapt these to the outputs of the target sensor using a trained CycleGAN filter (a type of trainable neural network).
Since the live detection is usually based on characteristic changes in the fingerprint images, the presented attack with the adapted images undermines the protective function in one go. During the attack, the IT researchers disrupt the SPI communication for every fourth image retrieved from the fingerprint sensor, for example, resulting in checksum errors. This leads to the cancellation (Cancel) of the CAMF gap and allows any number of fingerprint images to be checked. The number of the “disturbed” image varies from one smartphone model to another.
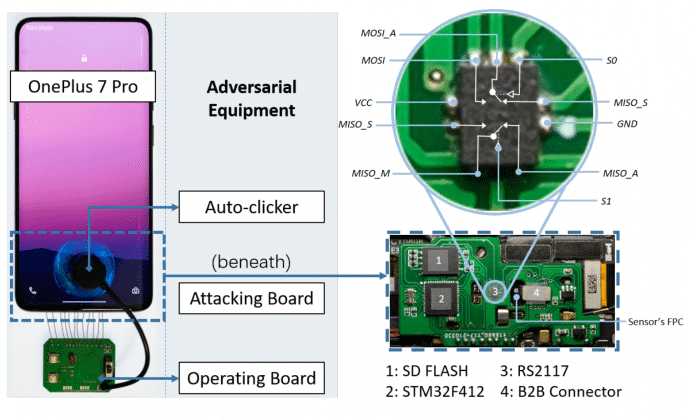
A small, inexpensive, home-made circuit board must be placed in the data lines between the fingerprint sensor and the cell phone mainboard. The auto-clicker also wakes up the sensor every second.
(Picture: Research paper on BrutePrint by Chen (Tencent) and He (Uni Zhejiang))
The hardware that the IT researchers use to carry out the attack is cheap and freely accessible – they had to spend around 15 US dollars: A microprocessor STM32F412 (Cortex M4) is used for SPI communication at around 38 MHz in slave mode used and controls the entire attack. A toggle switch RS2117 switches between the attack modes. A flash memory with 8 gigabytes of space is used to store around 200,000 fingerprint images in 8-bit grayscale and finally a connector is needed to connect the attack hardware on the cell phone and sensor side. An auto-click wakes up the fingerprint scanner every second at the behest of the STM32 MCU to automate the attack for a longer period of time.
Concrete attacks using BrutePrint
Chen and He explain that an attack looks like this: First, the back of the smartphone has to be removed and the connection between the fingerprint sensor and the cell phone motherboard has to be cut. Second, attackers must put the attack hardware into eavesdropping mode and capture fingerprint images. In the third step, they create the fingerprint dictionary from the fingerprint database based on the recognized format of the transmitted fingerprint images. The fourth step is the transfer of the fingerprint dictionary to the flash memory and the start of the automated attack.
The IT security researchers tested the BrutePrint attacks on ten standard smartphones. Of these, six were Android devices and two were HarmonyOS devices (Huawai) – there were endless attempts at authentication and smuggling in fingerprints from the dictionary. With the iPhone 7 and iPhone SE, both were not possible due to the encrypted SPI communication with authentication, among other things – the CAMF gap, however, made it possible to increase the number of login attempts from five to 15.
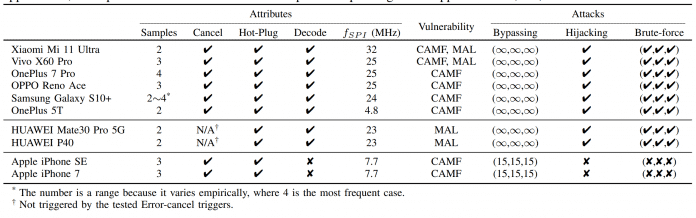
The devices tested with BrutePrint and the results. The Apple devices prevented the brute force attack with authentication and encrypted SPI communication.
(Picture: Research paper on BrutePrint by Chen (Tencent) and He (Uni Zhejiang))
In your The authors explain the research work in more detail, how they use reverse engineering to find out the image size of the fingerprint sensors, adapt the images from the database with CycleGAN and analyze the sensors’ proprietary protocols. They also report in detail on the attacks on the ten smartphone models.
The two IT researchers also make some suggestions for improvement. In order to prevent the CAMF attacks, manufacturers would have to introduce a counter for the canceled fingerprint checks. The transmission on the SPI bus must be secured. In addition, the timing for feedback on positive or negative tests should be the same and not provide shorter animations for positive results.
The CAMF vulnerability should be sealed with a firmware update, as should the MAL vulnerability. Although the attacks presented can be carried out with inexpensive hardware, they are probably more of interest to law enforcement agencies. If suspects’ smartphones to be searched have not been restarted, investigators could possibly use BrutePrint to gain access.
(dmk)

