Security researchers at CDN provider Akamai have described a new type of attack on Microsoft’s Active Directory. They are done via dynamic DNS registration by the Windows DHCP server. Attackers can spoof DNS entries, which can result in individual accounts or the entire Active Directory domain being compromised. If the Windows DHCP server is operated in the default settings, no credentials are required.
Advertisement
According to Akamai, Microsoft has no plans to deliver fixes at this time. In one Blog post The CDN provider presents details of the attacks and stops them Tool already to detect vulnerable configurations.
Dangerous updates of the second kind
The Active Directory is functionally closely linked to the DNS. In many cases, domain controllers are also used as DNS and DHCP servers. So that clients can store their host names as records in the DNS in environments with dynamic IP address assignment, Windows DHCP includes a dynamic DNS update. The client passes its FQDN in option 81 in the DHCP request to the DHCP server, which in turn carries out a dynamic DNS update (see figure). This means that the A records of the respective clients in the DNS are always updated with the assigned IP address. This feature is called DHCP DNS Dynamic Updates. No authentication from the DHCP client is used. These entries could therefore easily be spoofed.
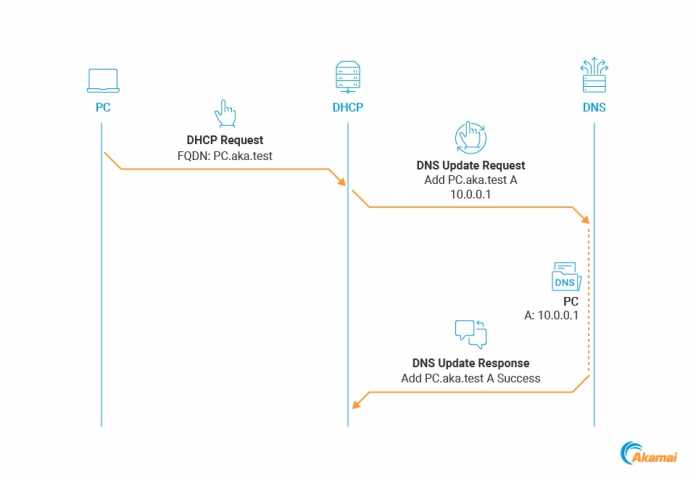
Process of dynamic DNS registration via DHCP server.
(Image: Akamai)
This is only possible for records that are not updated through Secure Updates. These are updates that come from the client and are not carried out via DHCP and DNS update by the DHCP server. These secure updates are authenticated and authorized via Kerberos and are therefore assigned to the client’s machine account. So-called client records created with this cannot be easily overwritten. However, managed records that were created by the DHCP server in the DNS server can be updated by the client without authentication. The same applies to the DNS entry of the DHCP server itself. According to Akamai, a spoofed DHCP update can overwrite a DNS entry for the DHCP server. If this is also a domain controller, this could have fatal consequences.
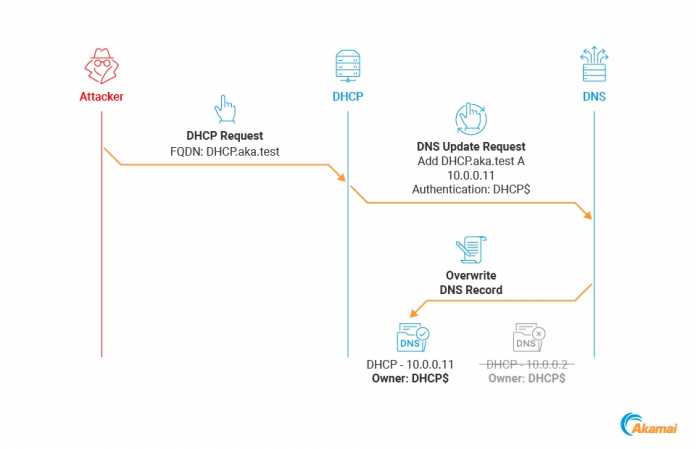
Spoofing the FQDN in the DHCP request from the client and subsequent update of the A record from the DHCP server in the DNS.
(Image: Akamai)
Countermeasures with weaknesses
As countermeasures, Akamai mentions name protection based on the DHCID record type (DHCP Client Identifier), which, according to the illustrations, also has some vulnerabilities, such as susceptibility to brute force attacks. It would also have to be active in all scopes. Another countermeasure would be to use dedicated DNS credentials for the interface between DHCP and DNS. However, records created by DHCP would still be vulnerable.
(ulw)

