Last night, Google released an update for the Chrome web browser that closes at least one critical security hole. It allows attackers to inject and execute malicious code.
Overall, the update includes corrections that close twelve security gaps, writes Google in the release announcement. Apparently, only six of these were reported by external IT security researchers, as only brief descriptions are available. According to this, at least one of the vulnerabilities is critical, four pose a high security risk and Google developers classify one as a medium threat.
Google Chrome: critical vulnerability
The most serious vulnerability that the new browser version fixes is a use-after-free vulnerability in the navigation component. The program code incorrectly accesses resources that have already been released, the content of which is therefore undefined and possibly contains or references malicious code. In the The developers explain the CVE entrythat it is a matter of memory scrambling on the heap that attackers “possibly can abuse by means of a manipulated website” (CVE-2023-2721, no CVSS value yet, risk according to Google “critical“).
Of the high-risk vulnerabilities listed, three are also use-after-free vulnerabilities, in the Autofill-UI, DevTools, and Guest-View components (CVE-2023-2722, CVE-2023-2723, CVE-2023-2725, without CVSS, high risk). A type confusion error can occur in the JavaScript engine V8, in which the data types used do not match and unintentional access to unintended memory areas can take place (CVE-2023-2724, no CVSS, high).
The bugs fix Chrome versions 113.0.5672.121 for iOS, 113.0.5672.126 for Linux and Mac, and 113.0.5672.126/.127 for Windows. Meanwhile, Google has upgraded the Extended Stable version of the web browser for Mac and Windows to version 112.0.5615.204.
version check
You can find out whether the current version is already active on the computer by clicking on the symbol with the three stacked dots to the right of the address bar and then on the path “Help” – “About Google Chrome”. This opens the version dialog. The displays the currently running version and starts the update process if necessary.
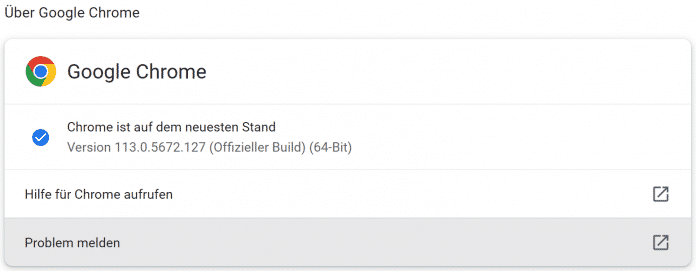
The Google Chrome version dialog shows the currently running version of the web browser and starts the update process if available.
(Image: Screenshot / dmk)
Under Linux, the distribution’s own software management usually delivers the updates. Users should therefore check the software management for updates there and have them applied when they are available. Since the vulnerabilities affect the underlying Chromium project, web browsers based on it, such as Microsoft Edge, should also deliver an update shortly. Users should also install these quickly.
Google last updated the Chrome web browser two weeks ago, closing 15 vulnerabilities in the process. In addition, the update to version branch 113 brought support for WebGPU – Chrome was the first browser to implement support for it.
(dmk)

